Quick Navigation:
- What Is 800-88 Data Erasure?
- Media Sanitization and Media Sanitization Process
- Key Principles of NIST 800-88 Data Erasure
- Benefits of NIST 800-88 Data Erasure
- Media Sanitization Methods
- Wipe Hard With NIST 800-88 Erasure Standard
- Conclusion
Data keeps businesses going in a world that is becoming more and more linked. It drives innovation, helps people make decisions, and runs operations. The question is, what happens to data when its lifecycle is over? It's not enough to delete files or format storage devices to ensure they are safe.
The NIST 800-88 Data Erasure guidelines are a complete set of rules to meet the important need for safe data destruction. These rules show how to properly clean private data on magnetic hard drives and mobile devices, keeping it safe from the ever-present risk of data breaches and unauthorized access.
NIST 800-88 is the standard for deleting data, and it helps businesses deal with the complicated world of data protection and government rules.

What Is 800-88 Data Erasure?
The National Institute of Standards and Technology is a well-known organization that sets standards and guidelines for many fields, including computer security. "Guidelines for Media Sanitization," a NIST Special Publication 800-88, tells you how to delete private data from different media and devices safely.
NIST 800-88 says that data erasure is the process of safely removing data from recording devices so that it can't be recovered in any way. It ensures that private data can't be accessed or put back together after being thrown away. It lowers the risk of data breaches and protects people's and businesses' privacy.
Media Sanitization and Media Sanitization Process
Media sanitization is the process of safely removing data from storage media so that it can't be accessed or recovered by people who aren't supposed to. This step is necessary to remove or reuse storage devices to ensure private data doesn't get into the wrong hands. The process of cleaning media usually has a few main steps.
The first step is to find the storage devices that hold private data. These could be hard drives, solid-state drives (SSDs), magnetic tapes, optical discs, or mobile devices. After figuring out what it is, the next step is to choose the right way to clean it based on the type of media, the data sensitivity, and any legal requirements.
Overwriting, degaussing, physical destruction, and cryptographic erasing are all common ways to clean something. Overwriting means replacing current data with random patterns more than once so that it can't be recovered. Magnetic fields are used to degauss and erase data from magnetic media. When the storage media are destroyed, the data can't be recovered.
Key Principles of NIST 800-88 Data Erasure
NIST 800-88 gives detailed instructions on how to delete data correctly, focusing on a few main principles:
1. Data Sanitization Methods
The publication outlines ways to clean different kinds of media, like mobile devices, solid-state drives (SSDs), magnetic hard drives, and optical media. Some of these ways are erasing data more than once in random patterns and damaging the storage media physically.
2. Verification and Validation
NIST 800-88 stresses the importance of checking and confirming that data deletion methods work. Companies should test carefully to ensure that data has been erased and can't be recovered using normal data recovery methods.
3. Documentation and Record-Keeping
For safety and auditing reasons, keeping good records of the data deletion process is important. Companies should keep careful records of when and how they erased data, including the type of media used, the method of erasure, and the results of any proof checks.
4. Risk Assessment
Before choosing a way to delete data, businesses should do a risk review to see how sensitive the data is, the possible effects of a data breach, and the rules. It helps determine the right amount of cleanliness needed to lower risks effectively.
Benefits of NIST 800-88 Data Erasure
Following the NIST 800-88 data erasure rules is good for businesses in several ways:
🛡️ Enhanced Data Security
By safely erasing data from storage devices, businesses can stop people from accessing them without permission and lower the risk of data breaches. It keeps private data from getting into the wrong hands.
🛡️ Regulatory Compliance
Following the NIST 800-88 guidelines helps businesses meet data dumping rules set by regulations like GDPR, HIPAA, and the PCI DSS, which helps them avoid expensive fines and penalties.
🛡️ Protection of Reputation
An organization can show its commitment to data security and privacy through proper data deletion practices, which builds trust among customers, partners, and other stakeholders.
🛡️ Cost Savings
Taking good steps to delete data lowers the chances of data breaches and the costs that come with them, like legal fees, fines, and damage to the company's image. In the long run, this saves the company money.
Media Sanitization Methods
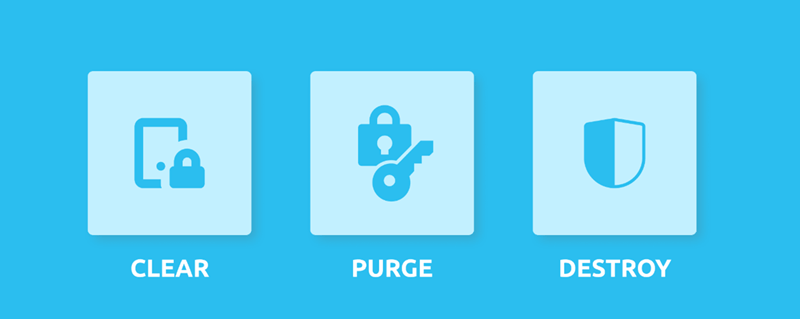
1. Clear
Cleaning electronic media means removing data from a storage device by deleting files, editing them, or using other standard methods. On the other hand, Clearing tries to replace data with new data so that it is less likely to be retrieved by basic data recovery tools. It differs from normal deletion methods that only remove file pointers.
This method works well for low-risk data and gadgets that will stay under the organization's control. It doesn't offer high protection against advanced data recovery techniques, though. Most of the time, clearing is the first step in sanitizing.
2. Purge
In contrast, purging is a safer way to clean up electronic media that is meant to make data unrecoverable in any way. Clearing may leave behind pieces of data that could be retrieved, but purging ensures that all data traces are erased from the storage media.
It is usually done by frequently writing over data with random patterns, erasing previous data and making it almost impossible to reconstruct. Purging is a good way to protect private data and devices sent to a place outside of the organization's control from data breaches and unauthorized access.
3. Destroy
The most extreme way to clean electronic media is to destroy it, damaging it to the point where data can't be recovered. It could mean burning optical discs, destroying hard drives, or crushing solid-state drives. Destroying ensures no data can be recovered, not even with the most powerful forensic methods.
Usually, this method is only used to get rid of very private or secret information that needs to be done safely and forever. The last step in the sanitization process is to destroy the storage media. It is usually done with proof that the media was destroyed.
Wipe Hard With NIST 800-88 Erasure Standard
Before you sell, donate or dispose of your old computer, you can use data erasure program to securely and permanently erase all data from the local hard drive.
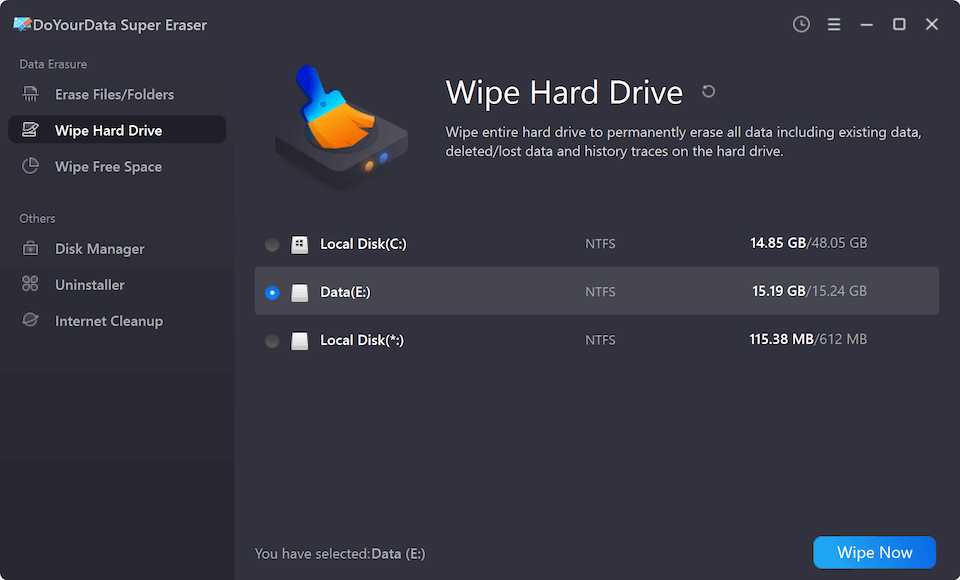
Step 1. Download and install the reliable data erasure program - DoYourData Super Eraser on your computer.
Step 2. Open DoYourData Super Eraser, choose Wipe Hard Drive mode, then select the local hard drive, click on Wipe Now button.
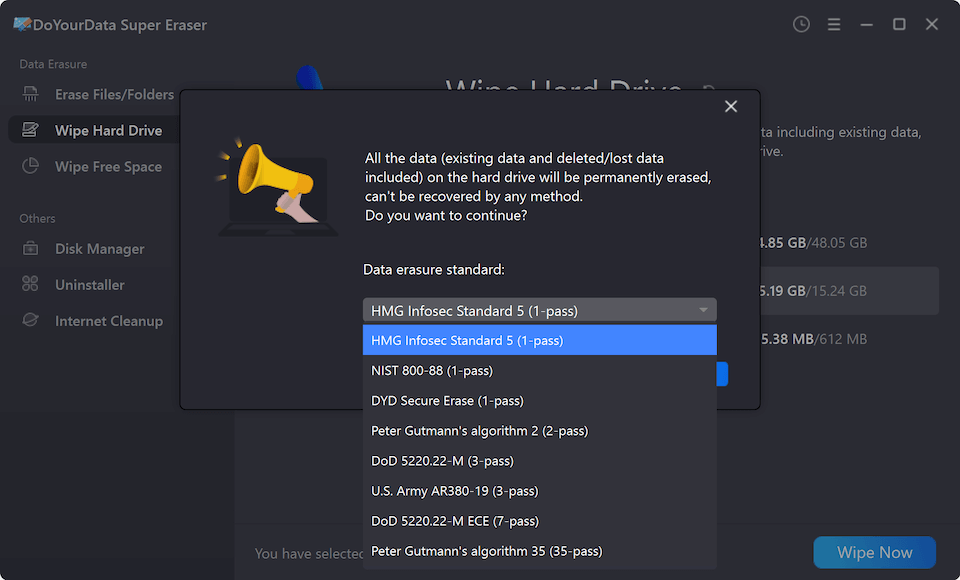
Step 3. Select NIST 800-88 as the erasure standard, then click on Continue button.
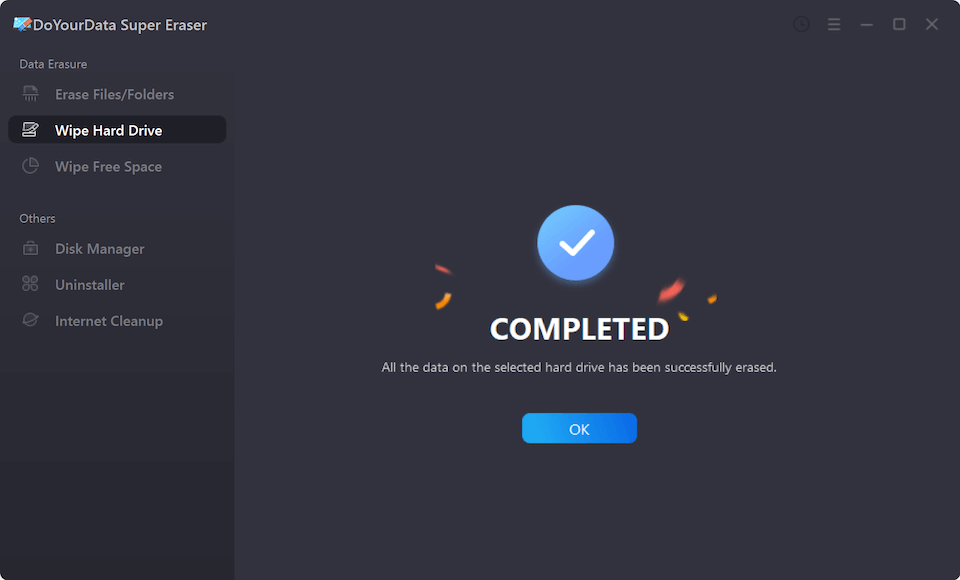
It will wipe the hard drive data with NIST 800-88 erasure standard. All data stored on the hard drive will be erased permanently, cannot be recovered by any method.
Conclusion:
In conclusion, the NIST 800-88 data erasure rules give you a complete plan for safely getting rid of sensitive data, protecting data privacy, and lowering the risk of data breaches. By following these rules, businesses can ensure they follow them, keep their reputations safe, and avoid the expensive fines for not following them. The result of using NIST 800-88 data erasure methods is that they make data safer, save money, and build stakeholder trust.

DoYourData Super Eraser
DoYourData Super Eraser, the award-winning data erasure software, offers certified data erasure standards including U.S. Army AR380-19, DoD 5220.22-M ECE to help you securely and permanently erase data from PC, Mac, HDD, SSD, USB drive, memory card or other device, make data be lost forever, unrecoverable!